Page History
On this page
| Table of Contents | ||
|---|---|---|
|
By default, communication between the Magic Collaboration Studio server and client is unencrypted. This page provides information on how to encrypt communication using TLS over TCP.
Generating a key pair using Java Keytool
To enable a secure connection between the client and the server, you need to generate two keystore files, each in their own keystores:
- KeyStore.jks (contains key and certificate) – server-side – upload it using Teamwork Cloud Admin console.
- cert.jks (contains public certificate) – client-side – add it using the Server Certificates option group in Environment Options.
To generate a key pair
- Go to your Java directory and open the folder named bin.
Enter keytool -genkey -alias MyDomain -keyalg RSA -keystore KeyStore.jks -keysize 2048 and press Enter.
Info You can give any name to MyDomain and KeyStore.jks.
Enter a password for your keystore and answer the questions asked. A certificate with a key is generated and placed into the keystore.
To extract a certificate without a key, type keytool -export -alias MyDomain -file certificate.cer -keystore KeyStore.jks and press Enter.
To place a certificate into another keystore, e.g. cert.jks, type keytool -import -alias MyDomain -file certificate.cer -keystore cert.jks and press Enter.
Info You can give any name to cert.jks. However, by default, the tool searches for this exact name.
Two keystore files are generated: one for the server (KeyStore.jks) and one for the client (cert.jks). You can now proceed to enable a secure connection between the client (modeling tool) and the server (Teamwork Cloud).
Enabling TLS encryption on server side
To enable a secure connection to Magic Collaboration Studio, you must enable TLS (Transport Layer Security) on the Teamwork Cloud Admin's Server Settings page. This page also allows you to disable the option if you do not need to use a secure connection (see the following figure). You can always enable it whenever necessary. The The most straightforward way to set up encryption is to use the keystore generated for Magic Collaboration Studio Teamwork Cloud and/or Web Application Platform. Locate and download the server Java KeyStore keystore (default: <install-_root>/MagicCollaborationStudio/TeamworkCloud/configuration/keystore.p12). Make a note of the password used for the KeyStorekeystore. If there is a corresponding public certificate (e.g. teamworkcloud.crt) on the server, download it as well. If there is no public certificate, use the following command to extract the public certificate from the Java KeyStore:keystore:
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
keytool -export -alias <teamworkcloud> -keystore <keystore.p12> -file <teamworkcloud.crt> |
| Info |
|---|
If you need to generate a new keystore, see Regenerating self-signed keystore. |
| Info |
|---|
The unencrypted port (default: 3579) remains active even after encryption is enabled. To prevent unencrypted connections, block the port at the firewall level. |
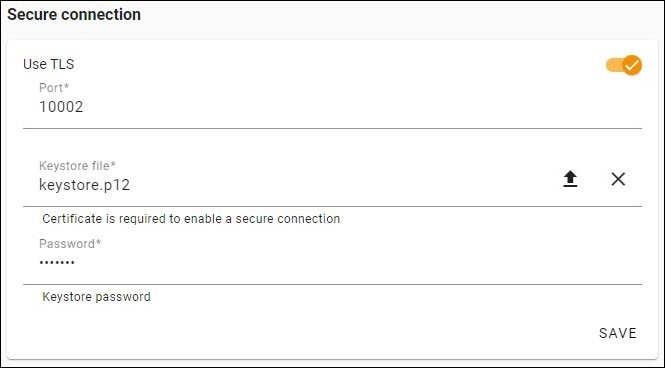
To enable a secure connection using the TLS protocol in Teamwork Cloud Admin
- Go to the Settings app.
- Move the slider to the right to enable the TLS protocol.
- Enter a custom port for encrypted communication, or keep default value of 10002.
- Upload the Java KeyStore keystore file, and type the password.
- Click Save.
Enabling TLS protocol in Teamwork Cloud
Admin (when the option is turned on, the color changes to orange).
Setting up client-side TLS
To enable a secure connection using the TLS protocol on the client-side, use the Server Certificates tool and provide the public certificate.
| Note |
|---|
The default port for a secure connection is 10002. If you are using another port for a secure connection instead of the default, append the port number to the server name in the Login dialog: dialog: |
| Warning |
|---|
The unecrypted port (3579) remains active even after TLS is enabled. Teamwork Cloud will continue to accept communication through both encrypted and unencrypted ports. Use firewall to disable port 3579 and block unencrypted communication. |
| Expand | ||||
|---|---|---|---|---|
| ||||
To enable a secure connection between the client and the server, you need to generate two keystore files, each in their own keystores:
To generate a key pair
|