Creating a TARA TableTo create a TARA Table
- In the Containment tree, right-click Risk Treatment and Cybersecurity Control and select Create Diagram.
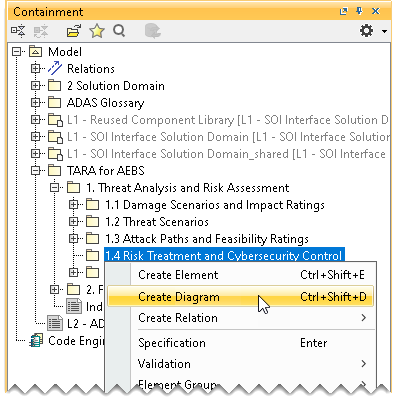
- Do one of the following:
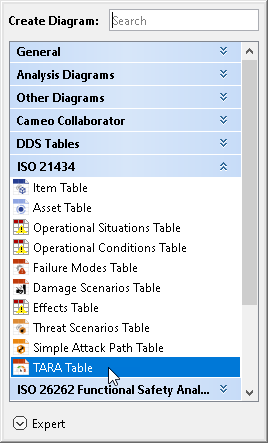
- In the dialog, expand ISO 21434 and select TARA Table.
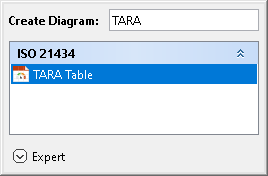
- In the search tab, type the keyword TARA and then select TARA Table.
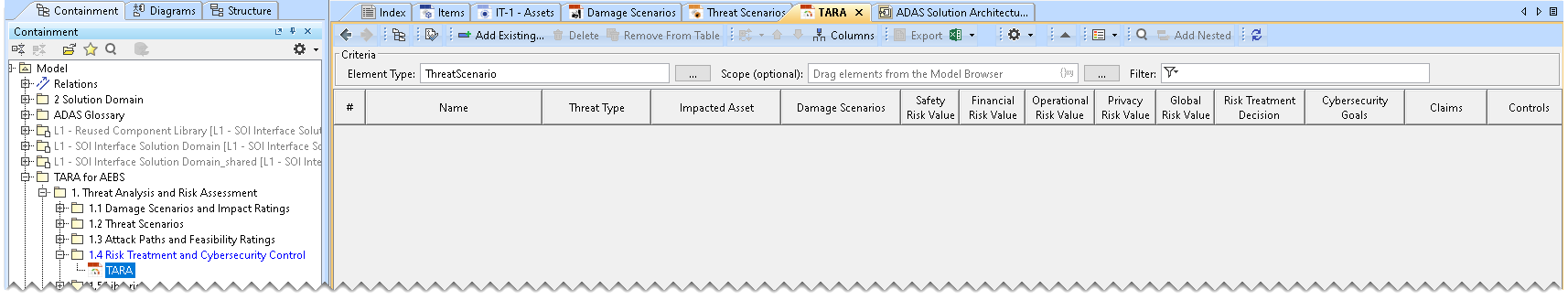
The TARA Table is displayed in the diagram pane of the modeling tool.
Adding Threat ScenariosTo add Threat Scenarios to the TARA Table
- In the TARA Table, click Add Existing.
- From the dialog, select the required Threat Scenario.
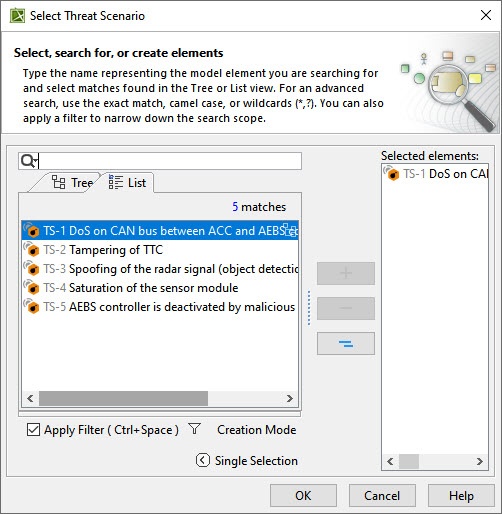
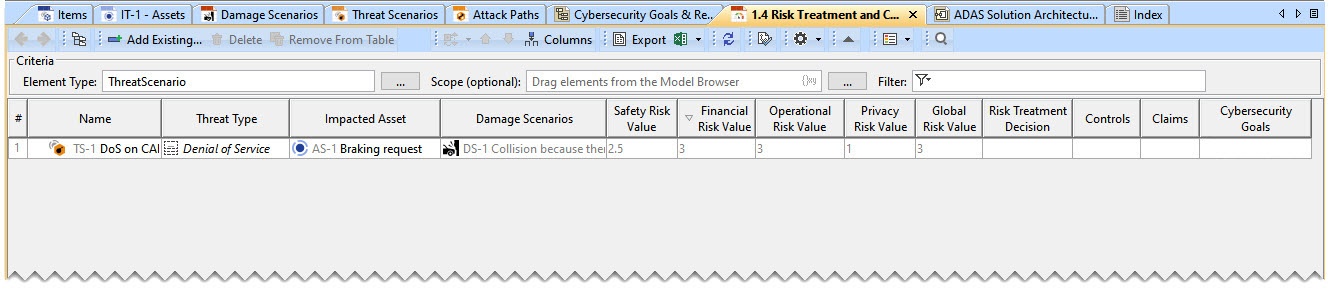
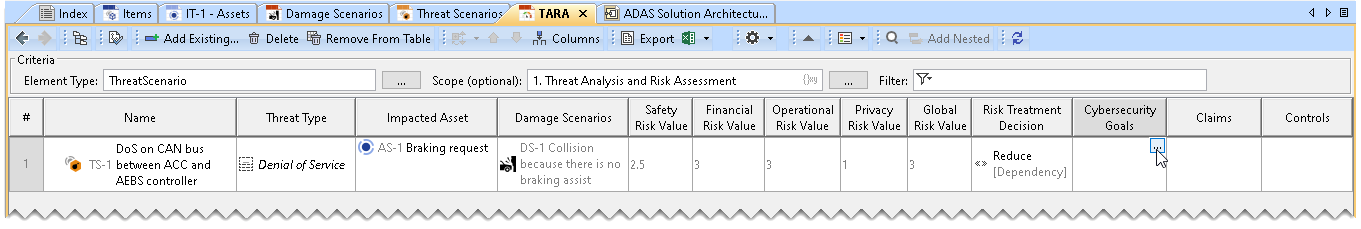
- Threat Type, Impacted Asset, and Damage Scenarios are automatically added to the TARA Table based on the Damage Scenario Table and Threat Scenarios Table.
- The risk values are automatically computed according to ISO/SAE 21434:2021 standard. Risk values are read-only values.
|
Assigning Risk Treatment Decision To assign Risk Treatment Decision
Adding Cybersecurity GoalTo add a Cybersecurity Goal to the TARA Table
-
 . .
- From the dialog, select Cybersecurity Goal.
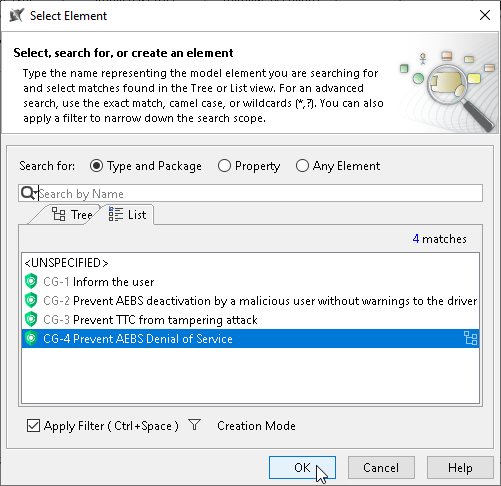
The Cybersecurity Goal is added to the TARA Table.
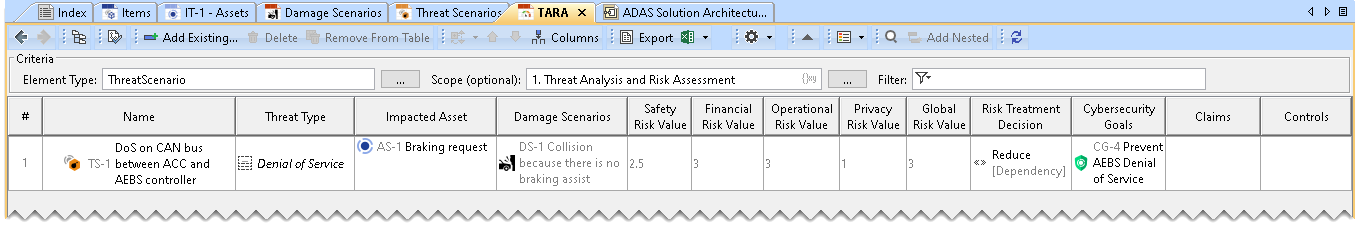
To add a Claim to the TARA Table
Adding ControlsTo add Controls to the TARA Table

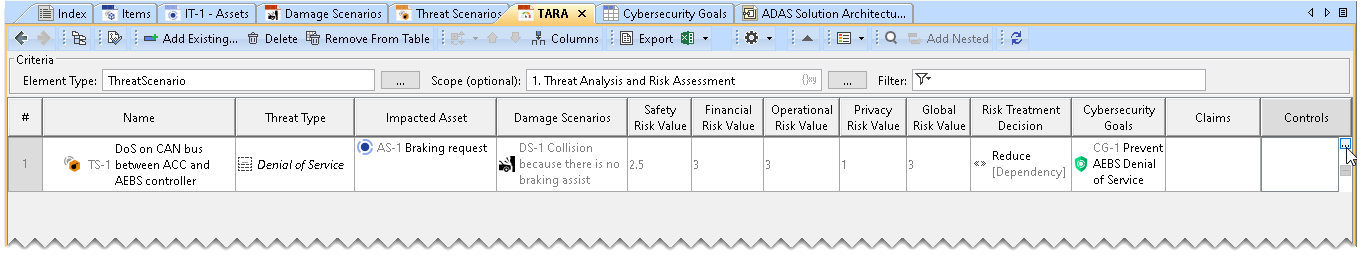
From the dialog, select Controls.
Controls are added to the TARA Table.
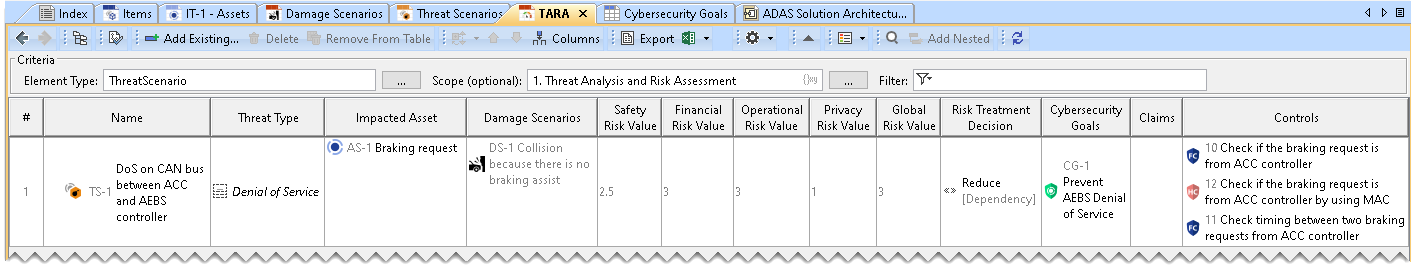
Controls are a list of Cybersecurity Requirements. There are 4 types of Cybersecurity Requirements: Functional, Technical, Hardware, and Software. |
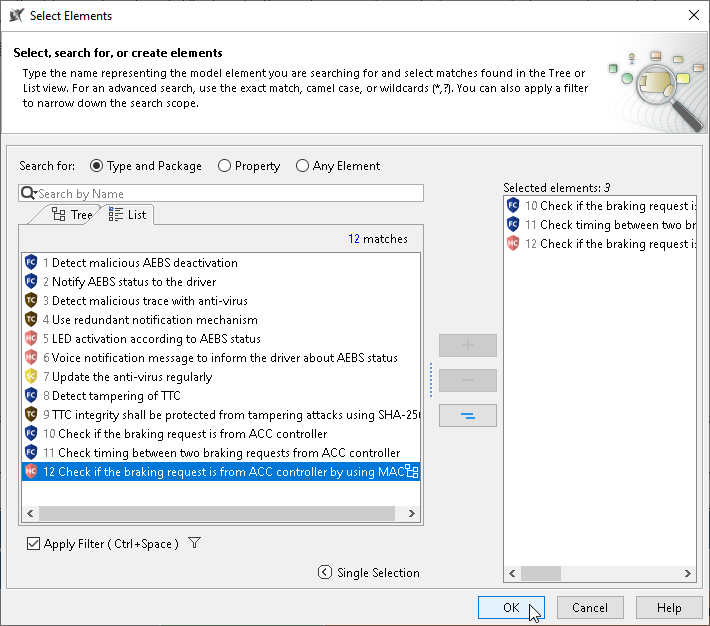
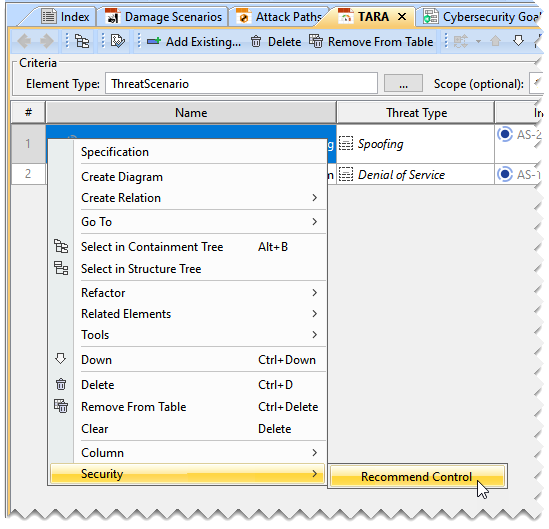
To ease the process of adding controls, the plugin provides you a feature to add the controls with the help of the Recommend Control command. The controls are recommended on the basis of assigned cybersecurity goals and CWE elements used as attack path steps. To add controls using the Recommend Control command to the TARA Table
- Right-click the threat scenario in the TARA table and select Recommended Control as follows:
From the Select Elements dialog, select or remove the recommended controls.
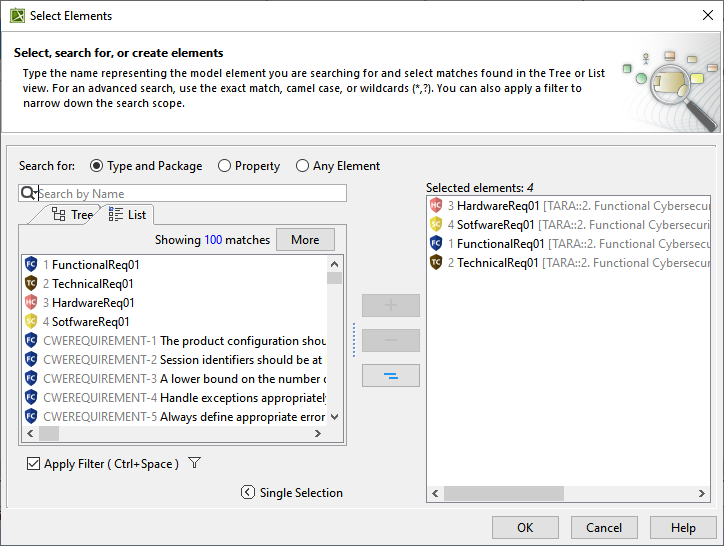
For requirements to be reflected as recommended controls in the Select Elements dialog either one of the conditions should be satisfied: - A Threat scenario should have assigned cybersecurity goals with derived requirements.
- A Threat scenario should have an attack path where the CWE elements are used in attack path steps.
|
The recommended controls are added to the TARA Table.
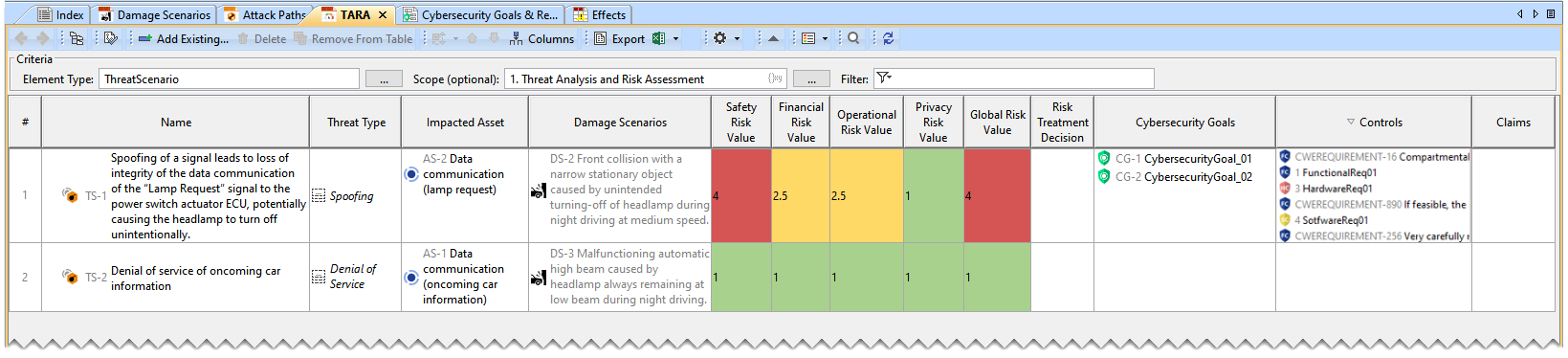
TARA 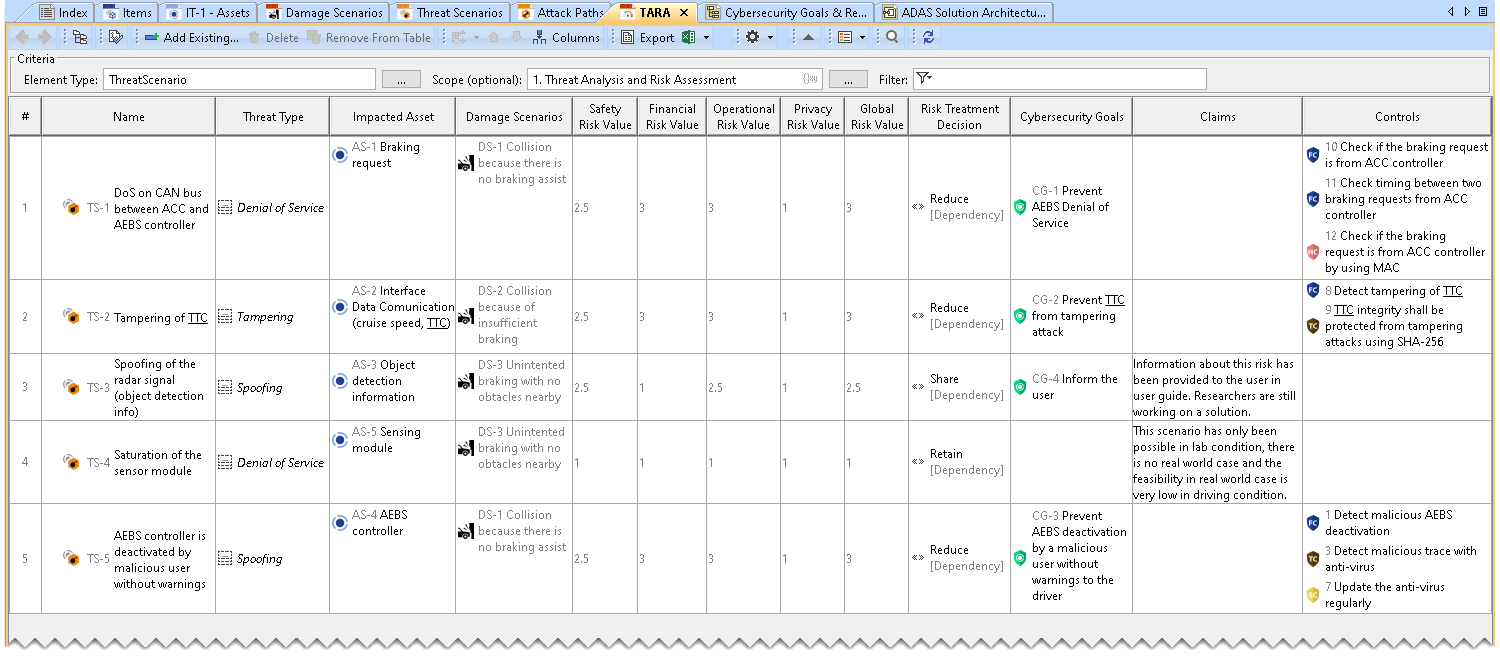
|