As an example of the process of adding and connecting to an LDAP server, let's suppose you want to add an LDAP server named Active Directory running on host 192.168.1.1. The default LDAP port is 389. If it is not the default, you must place the port number after a colon “:” (for example, 192.168.1.1:10389). The connection timeout is defined in milliseconds (ms) and specifies the period of response waiting time from the LDAP server. Following are the steps to add the LDAP server Active Directory using this example.
To add and configure an LDAP server
Click  to open the LDAP User Directories page.
to open the LDAP User Directories page.
Click  . The Create LDAP directory page will open to configure the LDAP server settings. This LDAP server connecting method is not set for Anonymous Bind, so the system username and password are required. The system username is normally authorized for querying other LDAP users in the LDAP directories. Make sure that the authorized system username and password are entered (full User DN system username is required). The connection information group must look like the following figure.
. The Create LDAP directory page will open to configure the LDAP server settings. This LDAP server connecting method is not set for Anonymous Bind, so the system username and password are required. The system username is normally authorized for querying other LDAP users in the LDAP directories. Make sure that the authorized system username and password are entered (full User DN system username is required). The connection information group must look like the following figure.
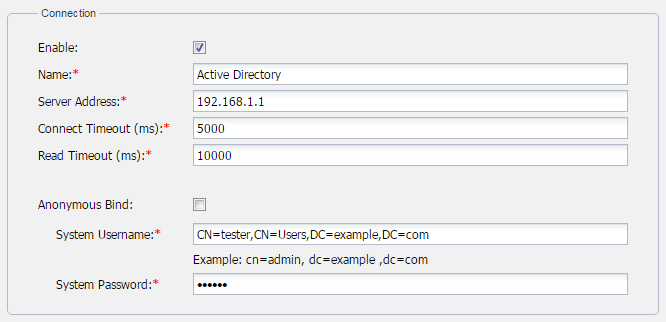
- Input the configuration properties to connect to the LDAP server.
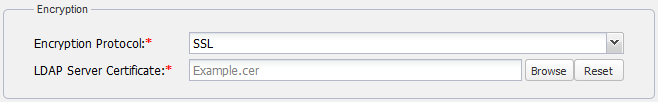
The LDAP server connection is secured with SSL protocol (LDAPS) at default port number 636. The Encryption Protocol must be SSL, and the LDAP server certificate file must be selected. The Encryption information group must look like the following figure.
Now the structure of the LDAP Active Directory in a tree view is as follows.
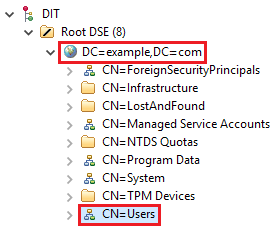
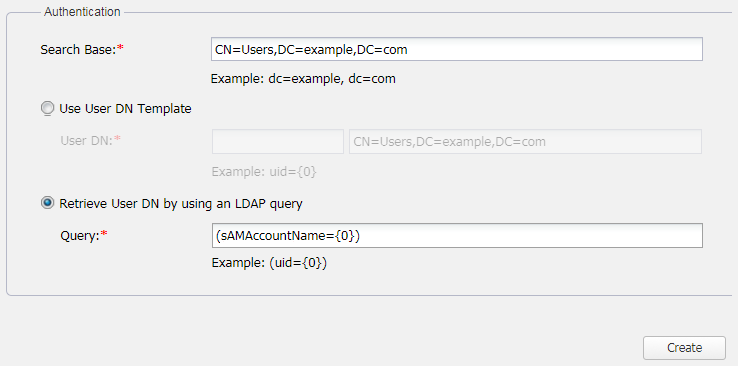
All LDAP users necessary to connect to Teamwork Cloud reside in CN=Users. The Search Base of this kind of LDAP server should be CN=Users,DC=example,DC=com. The pattern for the Search Base is {Parent_Of_LDAP_Users},{Grand_Parent_Of_LDAP_Users},…{n}.
The Retrieve User DN by using an LDAP query authentication method is selected by default. This Active Directory LDAP attribute name and value should be set to (sAMAccountName={0})”. Besides sAMAccountName, you can use any attribute name, but it must be followed with “={0}”. The Authentication information group is similar to the following figure.
- Click
 . The LDAP server's address and name will be added to the directory.
. The LDAP server's address and name will be added to the directory.