Definition
The Security Constraints (Sc-Ct) domain shows the security-related policy, guidance, laws and regulations as applicable to resources. It Specifies textual rules/non-functional requirements that are security constraints on resources, information and data (e.g. security-related in the form of rules (e.g. access control policy). A common way of representing access control policy is through the use of XACML (eXtensible Access Control Markup Language), it is expected that implementations of UAF allow users to link security constraints to external files represented in XACML.
Implementation
The Security Constraints (Sc-Ct) domain is represented by:
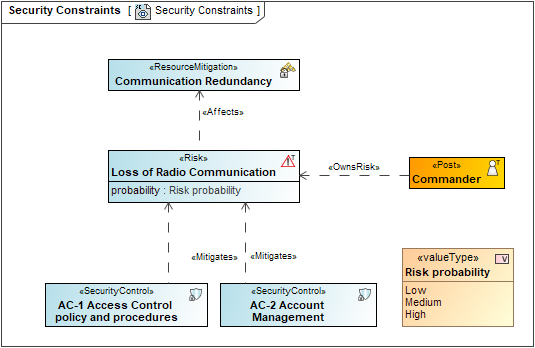
Sample
An example of the Security Constraints diagram
Related Elements
- Actual Responsible Resource
- Actual Risk
- Asset
- Function
- Measurable Element
- Measurement
- Measurement Set
- Operational Activity
- Operational Agent
- Operational Architecture
- Operational Mitigation
- Operational Role
- Property Set
- Resource Architecture
- Resource Mitigation
- Resource Performer
- Resource Role
- Risk
- Rule
- Security Constraint
- Security Control
- Subject Of Security Constraint
Related procedures